
Hovah Yii
My Hotmail Got Hacked: Lessons Learned and Steps to Take
Recently, I experienced the unsettling and distressing event of having my Hotmail account hacked. This incident not only disrupted my daily life but also provided me with valuable lessons on cybersecurity and the importance of vigilance in protecting personal information online. Here's what happened, what I learned, and the steps you can take if you find yourself in a similar situation.
The Incident
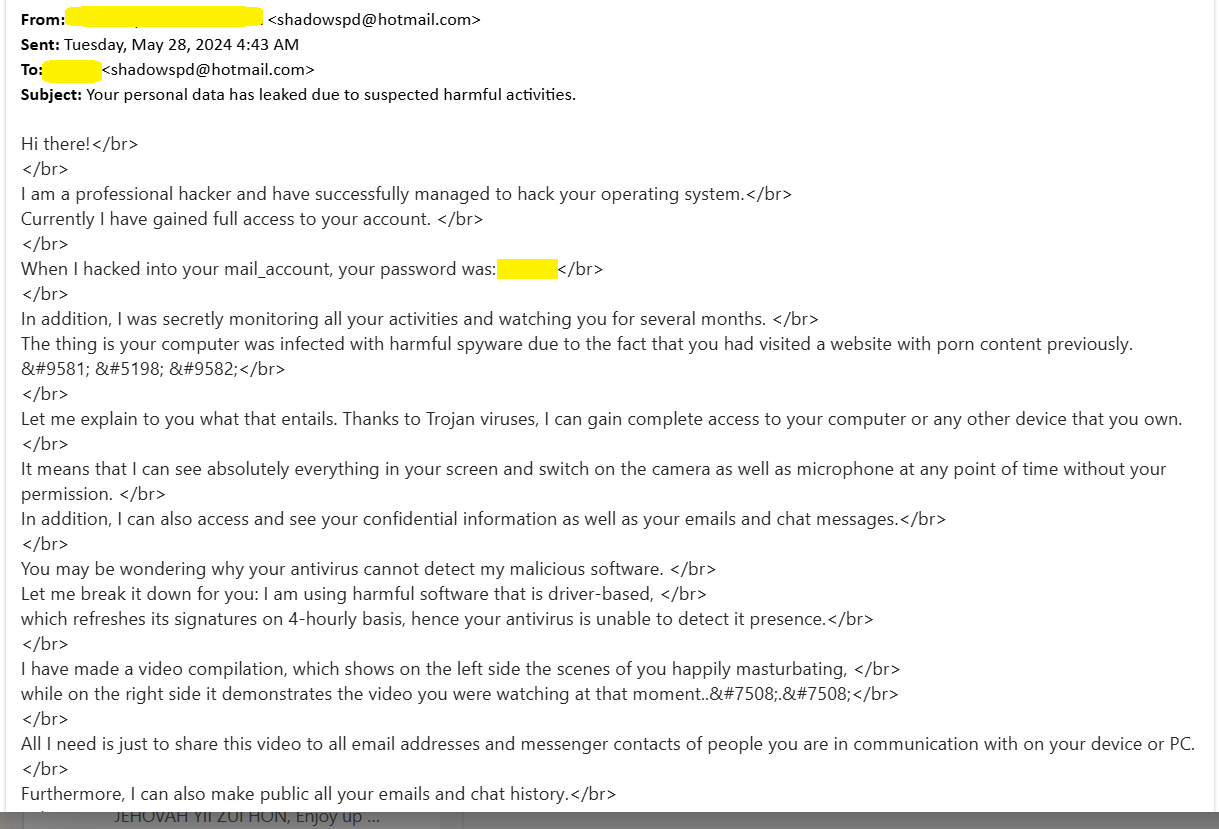
It all started on the morning of Tuesday, May 28, 2024, at 4:43 AM, when I received an email from an unknown sender. The email contained an old password associated with my Hotmail account, a password I had reset three months prior. This immediately raised alarms, as it indicated that my old password had been compromised.
What I Did Next
1️⃣ Verification and Security Checks:
- 👉 I confirmed that I could still access my Hotmail account and verified that my current password was different from the one mentioned in the suspicious email.
- 👉 I avoided clicking on any links or downloading attachments from the email.
- 👉 I scanned all my devices for malware and viruses to ensure their security.
2️⃣ Reporting the Incident: I decided to report the incident to the Cyber999 Cyber Incident Reference Center. Although I initially faced issues with the online form, I sent a detailed email to cyber999@cybersecurity.my. Here’s a template you can use:
Dear Cybersecurity Team, I am writing to seek urgent assistance regarding a concerning email I received, which may indicate a potential phishing attempt or security issue with my Hotmail account. Details of the Situation: Email Address: YourEmail@hotmail.com Date of Incident: [Insert Date] Description of Issue: I recently received an email from an unknown sender who shared an old password associated with my Hotmail account. I had reset this password three months ago. This email has caused me significant concern as it indicates that my old password may have been compromised. Actions Taken: - I verified that I can still access my Hotmail account and confirmed that my current password is different from the one mentioned in the suspicious email. - I have not clicked on any links or downloaded any attachments from the email. - I have scanned my devices for malware and viruses to ensure they are secure. Concerns and Questions: - I am concerned that my old password may have been leaked in a data breach, and this email could be part of a phishing attempt to gain further access to my account. - I would like to understand how the sender managed to send me an email containing my old password. - I am seeking guidance on additional steps I should take to secure my account and prevent any potential security breaches. Please advise on the best course of action at your earliest convenience. Your expertise and prompt assistance in this matter would be greatly appreciated. Thank you for your time and support. Sincerely, Your Name Contact Number Email Address
Cybersecurity Malaysia's Response
I was pleasantly surprised by the prompt response from Cybersecurity Malaysia. They provided detailed instructions on securing my email account and addressing potential vulnerabilities:
1️⃣ Addressing Email Security Issues:
- 👉 Verify and rectify issues related to DMARC, SPF, and DKIM to prevent email spoofing and ensure the authenticity of email communications. They provided helpful resources for troubleshooting these issues:
2️⃣ Changing Passwords and Enabling Multi-Factor Authentication (MFA):
- 👉 Change passwords for all accounts associated with the compromised email.
- 👉 Enable multi-factor authentication for added security.
3️⃣ Running Security Software:
- 👉 Download and run trusted security software to scan and protect devices from malware.
4️⃣ Lodging a Police Report:
- 👉 If needed, you can also lodge a police report with the Commercial Crime Division of the Royal Malaysia Police.
Additional Steps You Can Take
1️⃣ Monitor Device Activity:
- 👉 Check for suspicious applications running in the background by using tools like Task Manager on Windows or Activity Monitor on macOS.
- 👉 Use commands like # List established TCP connections
netstat -ano | findstr"ESTABLISHED"# Check details of a specific process (example PID: 24356) tasklist /FI "PID eq 24356"# Terminate the process if suspicioustaskkill /PID 24356 /F to identify suspicious connections and terminate them using appropriate commands.
2️⃣ Set Up Two-Factor Authentication (2FA):
- 👉 Enable 2FA on all accounts to add an extra layer of security.
3️⃣ Use Strong Passwords:
- 👉 Utilize password generators to create strong, unique passwords for each account.
4️⃣ Check for Data Breaches:
- 👉 Use services like Have I Been Pwned to check if your email or other personal information has been compromised in any data breaches.
Lessons Learned
Although this incident was unfortunate, it reinforced my belief in the importance of cybersecurity measures. The quick and efficient response from Cybersecurity Malaysia showed me that there are resources and people ready to help in times of need. Always be vigilant, take proactive steps to secure your accounts, and never hesitate to seek professional assistance when faced with a cyber threat.
The State of Cyber Attacks
Understanding the broader context of cyber attacks can help emphasize the importance of cybersecurity:
- ✅ By 2025, cybercrime will cost the world $10.5 trillion yearly.
- ✅ The entire cost of cyberattacks in 2022 was $6 trillion.
- ✅ 95% of data breaches are the result of human error.
- ✅ Globally, 30,000 websites are hacked daily.
- ✅ 64% of companies worldwide have experienced at least one form of cyber attack.
- ✅ There were 22 billion breached records in 2021.
- ✅ In 2021, ransomware cases grew by 92.7%.
- ✅ Email is responsible for around 94% of all malware.
- ✅ Every 39 seconds, there is a new attack somewhere on the web.
- ✅ An average of around 24,000 malicious mobile apps are blocked daily on the internet.
By sharing my experience, I hope to raise awareness and help others protect their digital lives from similar attacks.
Hovah Yii
Hovah, in his final year at University Malaysia Pahang studying Bachelor of Engineering Technology (Electrical) with Honours, is deeply involved in IoT research. A passionate reader and programmer, he has honed his skills through years as a student mentor at Chumbaka and as a freelance developer. Proficient in Next JS and Flutter frameworks, he has developed over seven web and two mobile apps, and contributed to backend code for business websites. Currently, he's collaborating with Go-Emerge Sdn Bhd on developing leica-store.my.